Note on Usage and Network Filtering
A 6to4 tunnel allows two servers in different countries to connect and exchange data as if they were on the same local network.Because many network filters are designed mainly for IPv4, traffic sent through 6to4 tunnels can sometimes pass older filtering systems that do not fully inspect IPv6 or encapsulated packets.
Important: This information is provided for general awareness.
While this behaviour can be useful for testing and research, tunnelling technologies must not be used to bypass lawful restrictions or government-imposed filtering.
Always follow local regulations and your provider’s acceptable use policy.
Introduction
A 6to4 tunnel encapsulates IPv6 packets inside IPv4 packets, allowing IPv6 communication across IPv4-only networks. This is particularly useful when your ISP does not support native IPv6, but you want IPv6 connectivity between sites. You typically need a 6to4 tunnel in the following cases:- Your devices are in two IPv6 networks but your provider doesn’t route IPv6 between them. → The 6to4 tunnel bridges the two IPv6 subnets using IPv4 transport.
- Your provider doesn’t support IPv6, but you want to send IPv6 traffic over IPv4 infrastructure. → The 6to4 tunnel encapsulates and forwards IPv6 packets between locations.
Network Topology
| Device | IPv4 Address | IPv6 Tunnel Address | IPv6 Subnet | Role |
|---|---|---|---|---|
| Mikrotik 1 | 45.153.127.87 | fd::1/126 | fe::/33 | Local router |
| Mikrotik 2 | 45.151.73.213 | fd::2/126 | fe:8000::/33 | Remote router |
- fe::/33 → used on Mikrotik 1’s network
- fe:8000::/33 → used on Mikrotik 2’s network
Getting Started: Prerequisites
Before you begin:- Ensure both MikroTik routers have public IPv4 addresses (no NAT).
- Enable the IPv6 feature (RouterOS v7 syntax):
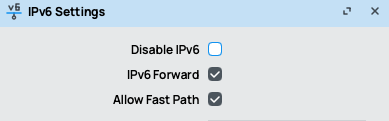
- Access both routers via Winbox or SSH.
- This guide is written for RouterOS v7.x (v7.12 or later recommended).
Step 1 – Create the 6to4 Tunnel Interface
Create a 6to4 tunnel on both routers, specifying the local and remote IPv4 addresses, and enable IPsec encryption using an ipsec-secret.On Mikrotik 1
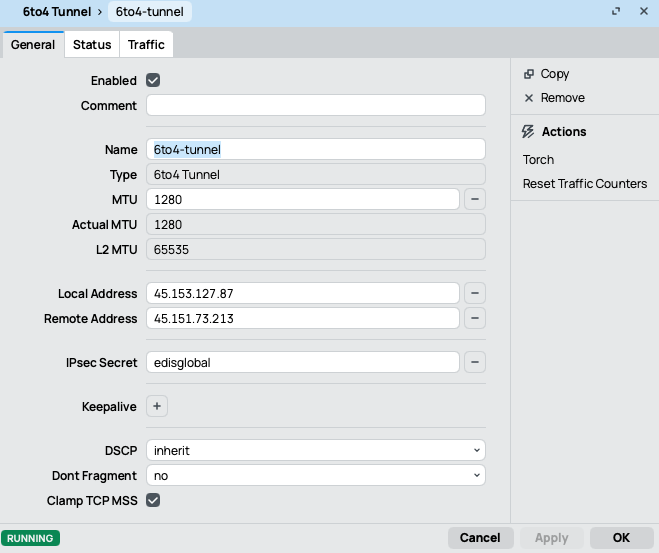
On Mikrotik 2
Step 2 – Assign IPv6 Addresses
Assign IPv6 addresses to the 6to4 tunnel for connectivity and to each router’s internal network using their respective /33 subnets.On Mikrotik 1
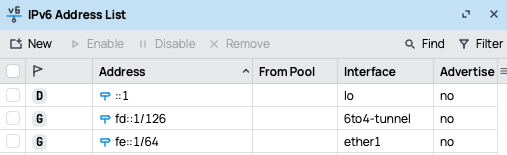
On Mikrotik 2
Step 3 – Add IPv6 Routes
Each router must know how to reach the other router’s /33 subnet through the 6to4 tunnel.On Mikrotik 1
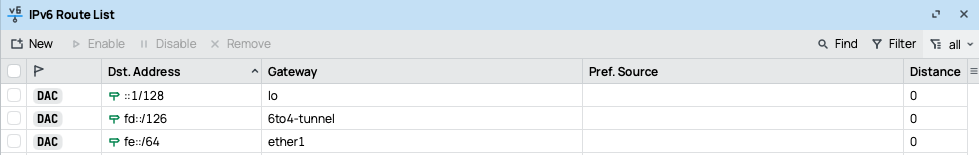
On Mikrotik 2
- fe::/33 → local network of Mikrotik 1
- fe:8000::/33 → remote network on Mikrotik 2
- The gateway value is the remote IPv6 tunnel address (fd::1 or fd::2).
Step 4 – Test the Tunnel
Test IPv6 connectivity between both routers and their LANs.From Mikrotik 1
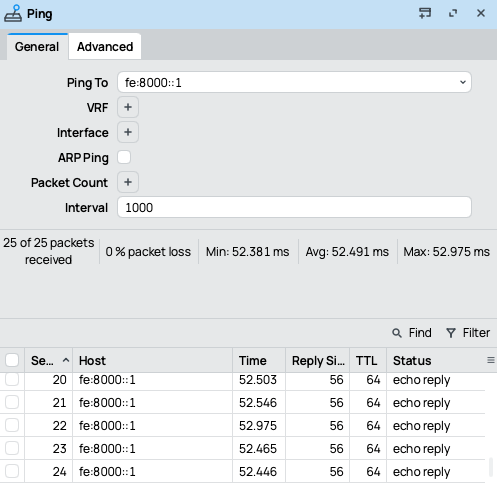
From Mikrotik 2
Troubleshooting
If the tunnel doesn’t work as expected:- Confirm both routers have public IPv4 connectivity.
- Check that IPv6 is enabled globally.
- Ensure the same ipsec-secret value is used on both routers.
- Allow protocol 41 (IPv6 encapsulation) and IPsec traffic in the firewall.
- Keep MTU set to 1280 to avoid fragmentation.